Understanding the Lockheed Martin Cyber Kill Chain: A Key Framework for Defending Against Cyber Threats
In the ever-evolving world of cybersecurity, staying ahead of attackers is a constant challenge. Hackers are becoming more sophisticated, and the methods they use are more complex than ever before. To help security professionals better understand and respond to these threats, Lockheed Martin developed a model known as the Cyber Kill Chain.
The Lockheed Martin Cyber Kill Chain is a strategic framework that breaks down the typical phases of a cyberattack, from the early reconnaissance stage all the way through to the final action the attacker wants to achieve, like data theft or system disruption. By breaking the attack down into phases, the Cyber Kill Chain helps cybersecurity teams identify, stop, and mitigate attacks before they cause significant damage.
What is the Cyber Kill Chain?
The Cyber Kill Chain is essentially a roadmap for how cyberattacks are executed. Originally based on military models of the kill chain (used to describe the process of identifying, targeting, and neutralizing a threat in warfare), Lockheed Martin adapted the concept to fit the cybersecurity landscape. The idea is simple: just as in military engagements, stopping the attack at any phase of the chain can neutralize the threat before it reaches its goal.
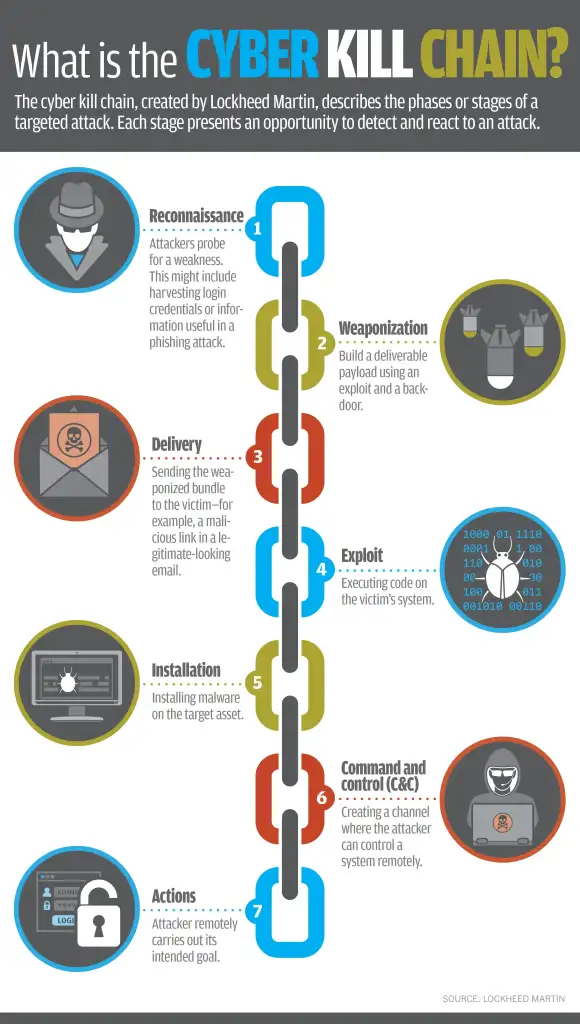
The Cyber Kill Chain consists of seven distinct phases, each representing a step in a cyberattack:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (C2)
- Actions on Objectives
Here’s an in-depth exploration of each phase of the Lockheed Martin Cyber Kill Chain and how defenders can implement security controls to break each link in the chain.
- Reconnaissance: In this phase, attackers begin by gathering as much information as possible about the target. This could include passive methods, like scanning public websites and collecting data from social media, or more active tactics like scanning for open ports and services. The goal of reconnaissance is to identify vulnerabilities that can be exploited later.
- Breaking the Chain: To thwart attackers during this phase, security teams can:
- Implement network monitoring: Use intrusion detection systems (IDS) or intrusion prevention systems (IPS) to detect and log reconnaissance activities such as unusual scanning patterns.
- Minimize your attack surface: Reduce the amount of publicly available information, especially sensitive data, by conducting regular audits of web presence, domain registrations, and any exposed services.
- Use deception technologies: Deploy honeypots or decoy systems that can trick attackers into thinking they’ve found a legitimate target, thus exposing their reconnaissance attempts.
- Breaking the Chain: To thwart attackers during this phase, security teams can:
- Reconnaissance: In this phase, attackers begin by gathering as much information as possible about the target. This could include passive methods, like scanning public websites and collecting data from social media, or more active tactics like scanning for open ports and services. The goal of reconnaissance is to identify vulnerabilities that can be exploited later.
- Weaponization: During weaponization, attackers create their malicious payload, often by pairing an exploit (e.g., a vulnerability in software) with a backdoor or other type of malware. This could involve building a Trojan horse, a macro-laden document, or another form of malware designed to infiltrate the target.
- Breaking the Chain: Disrupting this phase involves:
- Vulnerability management: Keep software up to date with patches and security updates to prevent attackers from using known vulnerabilities in their payloads.
- Threat intelligence sharing: Collaborate with industry partners to stay informed of the latest threat actor tactics and malware developments. This can help in identifying new payloads or tools before they reach your environment.
- Security awareness training: Educate employees on the dangers of opening unsolicited attachments, executing macros in documents, or downloading files from untrusted sources.
- Breaking the Chain: Disrupting this phase involves:
- Weaponization: During weaponization, attackers create their malicious payload, often by pairing an exploit (e.g., a vulnerability in software) with a backdoor or other type of malware. This could involve building a Trojan horse, a macro-laden document, or another form of malware designed to infiltrate the target.
- Delivery: In the delivery phase, the attacker transmits the weaponized payload to the victim. This could be via email (phishing), web downloads, USB drives, or other forms of file transfer. The method of delivery depends on the vulnerabilities and weak points identified in the reconnaissance phase.
- Breaking the Chain: Effective security measures for this phase include:
- Email filtering: Implement advanced email filtering solutions that can detect and block phishing attempts and suspicious attachments. Use technologies like sandboxing to analyze potentially malicious files before they reach end-users.
- Web security gateways: Employ web proxies and security gateways that can block access to known malicious sites and prevent users from downloading malicious content.
- USB restrictions: Lock down USB ports on corporate devices or implement data loss prevention (DLP) solutions to control unauthorized data transfers.
- Breaking the Chain: Effective security measures for this phase include:
- Delivery: In the delivery phase, the attacker transmits the weaponized payload to the victim. This could be via email (phishing), web downloads, USB drives, or other forms of file transfer. The method of delivery depends on the vulnerabilities and weak points identified in the reconnaissance phase.
- Exploitation: Once the payload is delivered, the exploitation phase begins. The attacker takes advantage of a vulnerability on the target system to execute malicious code. This could be a software bug, an unpatched system, or a social engineering trick that convinces the victim to execute the payload themselves.
- Breaking the Chain: To prevent exploitation:
- Application whitelisting: Only allow pre-approved applications to run on your systems, preventing unauthorized or malicious programs from executing.
- Endpoint protection: Deploy advanced endpoint detection and response (EDR) tools that can identify and block malicious activity in real time, even if it hasn’t been seen before.
- Regular patching: Ensure that all systems, including third-party applications, are regularly patched to close known vulnerabilities.
- Breaking the Chain: To prevent exploitation:
- Exploitation: Once the payload is delivered, the exploitation phase begins. The attacker takes advantage of a vulnerability on the target system to execute malicious code. This could be a software bug, an unpatched system, or a social engineering trick that convinces the victim to execute the payload themselves.
- Installation: After exploiting the vulnerability, the attacker installs the malware on the victim’s system. This often includes installing backdoors, keyloggers, ransomware, or other malicious programs to gain persistent access to the system.
- Breaking the Chain: Defending against this phase involves:
- Endpoint hardening: Configure systems to reduce the chances of malware installation, including disabling unused services, enabling Secure Boot, and enforcing least privilege principles.
- Endpoint detection and response (EDR): Use EDR solutions to detect unusual activities related to the installation of malware, such as the creation of new registry keys or scheduled tasks that aren’t part of regular operations.
- Behavioral analysis: Leverage machine learning and behavior-based analysis to detect anomalies that may indicate malware is being installed, such as unauthorized software executing with elevated privileges.
- Breaking the Chain: Defending against this phase involves:
- Installation: After exploiting the vulnerability, the attacker installs the malware on the victim’s system. This often includes installing backdoors, keyloggers, ransomware, or other malicious programs to gain persistent access to the system.
- Command and Control (C2): What it is: In the command and control phase, the attacker establishes a communication channel back to their own infrastructure to control the compromised system. Through this channel, they can issue commands, exfiltrate data, or spread malware laterally across the network.
- Breaking the Chain: Security controls that disrupt this phase include:
- Network segmentation: Isolate critical assets by segmenting your network. Even if an attacker establishes control of one system, segmentation can limit their ability to communicate with other systems.
- DNS monitoring and blackholing: Monitor DNS requests and block attempts to resolve known malicious domains. Implement sinkholing to reroute C2 traffic to a controlled environment for analysis.
- Threat intelligence feeds: Use up-to-date threat intelligence feeds that include known malicious IP addresses and domains associated with C2 infrastructure. Automatically block these in firewalls and intrusion prevention systems.
- Breaking the Chain: Security controls that disrupt this phase include:
- Command and Control (C2): What it is: In the command and control phase, the attacker establishes a communication channel back to their own infrastructure to control the compromised system. Through this channel, they can issue commands, exfiltrate data, or spread malware laterally across the network.
- Actions on Objectives: The final phase is where the attacker carries out their ultimate goal, whether that’s data theft, system destruction, encryption (ransomware), or establishing further persistence. This is the moment of impact, where the attacker attempts to complete their mission.
- Breaking the Chain: If the attacker reaches this phase, damage mitigation is critical:
- Data encryption and integrity controls: Ensure sensitive data is encrypted, both at rest and in transit, so that even if attackers exfiltrate it, they can’t easily use it. Additionally, maintain strong integrity controls to detect unauthorized changes to critical systems.
- User activity monitoring: Implement monitoring solutions that provide visibility into user activity. This can help detect abnormal behavior, such as unauthorized access to sensitive files or databases, before the attacker completes their objective.
- Incident response readiness: Be prepared with a robust incident response plan. Once an attack is detected, swift containment and remediation are critical to limiting the impact. This includes having a backup strategy, disaster recovery plan, and cross-functional teams ready to act.
- Breaking the Chain: If the attacker reaches this phase, damage mitigation is critical:
- Actions on Objectives: The final phase is where the attacker carries out their ultimate goal, whether that’s data theft, system destruction, encryption (ransomware), or establishing further persistence. This is the moment of impact, where the attacker attempts to complete their mission.
Each of these phases represents a point where defenders can potentially disrupt the attack, either by detecting malicious activity, preventing further escalation, or neutralizing the threat before damage is done. It’s a way of thinking that allows defenders to not only respond to attacks in progress but also proactively prepare for and mitigate potential threats.
Why is the Cyber Kill Chain Useful?
The Lockheed Martin Cyber Kill Chain is useful for several key reasons:
- Understanding Attack Patterns: The Cyber Kill Chain helps security professionals understand the structure of an attack. Rather than seeing a cyberattack as a single event, the Kill Chain breaks it down into actionable stages. This granular approach allows defenders to anticipate the next steps an attacker might take.
- Proactive Defense: By mapping out the phases of a potential attack, the Cyber Kill Chain allows organizations to implement proactive defenses at every stage. For example, if you know attackers tend to start with reconnaissance, you can focus on detecting suspicious scanning of your network or prevent unauthorized access to public-facing systems.
- Early Detection: One of the most significant benefits of the Cyber Kill Chain is that it encourages early detection. Identifying and stopping an attack early—before the attacker can establish control over a system—can prevent significant damage. By monitoring for signs of activity at each phase, security teams have multiple opportunities to stop an attack.
- Incident Response Planning: The Cyber Kill Chain also aids in incident response by giving security teams a structured model to follow during and after an attack. By understanding which phase the attack has reached, defenders can tailor their response efforts more effectively and focus on containing and remediating the threat.
- Continuous Improvement: The Cyber Kill Chain provides a framework for continuous improvement in cybersecurity defense. After responding to an attack, security teams can analyze which phase of the Kill Chain was breached and adjust their defenses accordingly, strengthening areas of vulnerability and improving detection mechanisms.
- Attack Simulation and Training: Security teams can also use the Cyber Kill Chain to simulate attacks and run red team exercises. By walking through each phase of the Kill Chain, teams can practice identifying and responding to threats, improving their preparedness for real-world incidents.
The Lockheed Martin Cyber Kill Chain is a powerful framework for understanding, defending against, and responding to cyberattacks. It offers a structured way to break down attacks into manageable stages, allowing for more targeted and effective defenses. Whether you’re running a security operations center, developing incident response plans, or training your security team, the Cyber Kill Chain is a valuable tool that helps keep you one step ahead of attackers.