Understanding the MITRE ATT&CK Framework: A Powerful Tool in Cybersecurity
In today’s digital age, the world of cybersecurity is often described as a game of cat and mouse. Hackers are constantly finding new ways to break into systems, while security professionals work tirelessly to stop them. One of the most powerful tools that security teams have at their disposal is the MITRE ATT&CK Framework. But what exactly is it, why was it created, and how do security teams use it to keep organizations safe? Let’s break it down in simple, non-technical terms.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework is like a detailed map of all the ways hackers can break into computer systems and networks. Imagine you’re a detective working on a crime scene, just like how a detective knows the different tactics criminals use, security teams use the MITRE ATT&CK Framework to understand the tactics and techniques that cybercriminals use to attack organizations.
ATT&CK (which stands for Adversarial Tactics, Techniques, and Common Knowledge) was created by MITRE, a non-profit organization that supports the U.S. government in areas like cybersecurity. Essentially, ATT&CK is a huge database or library that catalogs real-world techniques used by hackers. It describes specific methods attackers use to infiltrate systems, maintain access, and achieve their goals, like stealing data or causing disruptions.
Why Was MITRE ATT&CK Created?
MITRE ATT&CK was designed to help security teams understand and defend against cyber threats in a more structured and informed way. Before ATT&CK, security teams didn’t have a standardized way of describing what attackers were doing. The framework was created to give everyone a common language and set of terms so that teams could communicate more effectively about the specific tactics and techniques being used by attackers.
It was also designed to improve how organizations detect, respond to, and learn from cyberattacks. By cataloging and organizing the various methods attackers use, MITRE ATT&CK helps security teams think like hackers, anticipating their moves and building defenses that are stronger and more proactive.
How is the MITRE ATT&CK Framework Used?
While the framework itself may seem complex, it’s a highly practical tool for several key players in cybersecurity. Here’s how it’s used in simple terms:
- Cybersecurity Teams: Cybersecurity teams use the MITRE ATT&CK Framework to understand how hackers might try to break into their systems. The framework provides a “playbook” of sorts, detailing the steps hackers take and how they combine different techniques. This helps cybersecurity professionals stay ahead of attackers by knowing what to look for. For example, if a company is targeted by a phishing email, the cybersecurity team can use the framework to understand what the next move from the hacker might be.
- Incident Response Teams: When an attack happens, incident response teams are the ones who swoop in to investigate and mitigate the damage. The MITRE ATT&CK Framework helps these teams figure out exactly how the attack happened by breaking it down step by step. For example, if malware was used in the attack, the framework can help the team identify which specific techniques were used and what the attacker’s goal was. This helps them respond more quickly and effectively.
- Threat Hunting Teams: Think of threat hunting teams as proactive detectives. Instead of waiting for an attack to happen, they go searching for evidence that an attacker is already in the system or trying to break in. They use the MITRE ATT&CK Framework to guide their search by focusing on the techniques that attackers commonly use. This helps them find potential threats early, before they cause damage.
- Computer Forensic Teams: After an attack or breach, forensic teams come in to analyze the digital evidence. The MITRE ATT&CK Framework provides them with a roadmap of what to look for in their investigation. By comparing the actions of the attacker to the techniques listed in the framework, forensic teams can determine how the attacker got in, what they did once inside, and how to prevent similar attacks in the future.
Why is MITRE ATT&CK So Useful?
One of the key reasons the MITRE ATT&CK Framework is so valuable is that it provides a common language for cybersecurity professionals. Whether they’re working in different organizations or across the globe, security teams can use the framework to talk about attacks in a clear and standardized way. This makes it easier to share information, collaborate, and improve defenses.
Additionally, the framework is based on real-world observations. The techniques listed in MITRE ATT&CK aren’t theoretical, they’re actual methods that have been used by hackers in the past. This makes the framework incredibly practical and relevant for defending against modern threats.
Putting It All Together
In simple terms, the MITRE ATT&CK Framework is a powerful tool that helps security professionals understand and defend against cyber threats. By breaking down the different ways hackers operate, it enables organizations to detect, respond to, and learn from attacks more effectively. It’s like having a playbook for defending your home from burglars, except, in this case, the burglars are hackers, and the home is your organization’s digital infrastructure.
Whether you’re a member of a cybersecurity team, an incident responder, a threat hunter, or a computer forensic analyst, the MITRE ATT&CK Framework offers a clear and structured way to think about and fight back against cyberattacks.
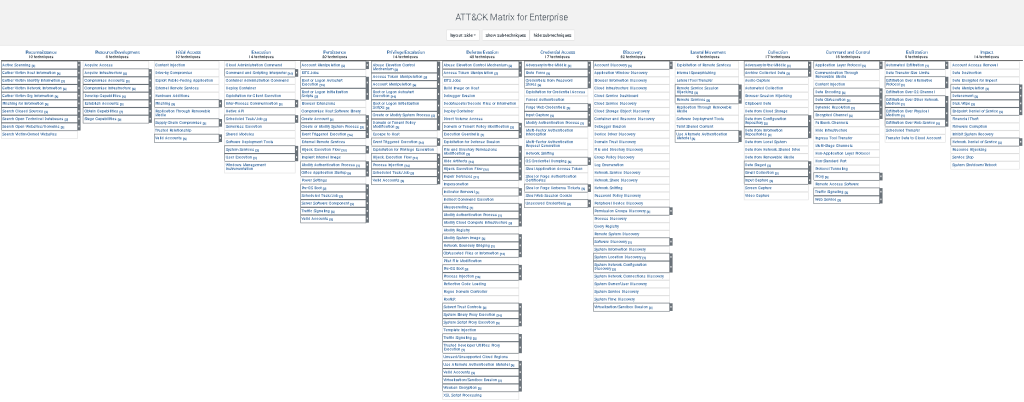
Let’s explore the sections of the MITRE ATT&CK Framework. These sections, also known as tactics, represent the major goals or objectives that an attacker seeks to accomplish during an attack. Each tactic is a stage in the attack process, and within each stage, various techniques are used to achieve the objective.
- Initial Access: The goal of this tactic is to gain a foothold inside the target network. Attackers typically start by exploiting vulnerabilities in external systems, such as through phishing, exploiting public-facing applications, or using supply chain compromises.
Common Techniques:
- Phishing: Sending fraudulent emails to trick users into providing credentials or clicking on malicious links.
- Drive-by Compromise: Getting a user to visit a compromised website that automatically downloads malware.
- Exploitation of Public-Facing Applications: Exploiting vulnerabilities in externally accessible systems.
Why It Matters: Initial access is the entry point into the network. Security controls that stop the attacker here, like email filtering, anti-phishing training, or web application firewalls, can prevent an attack before it even begins.
- Execution: After gaining initial access, the next step for the attacker is to execute malicious code within the target environment. This could be the launch of malware, scripts, or commands that further compromise the system.
Common Techniques:
- Command-Line Interface: Attackers use commands to execute code or scripts on the victim’s machine.
- Scripting: Using tools like PowerShell, VBScript, or Python to automate tasks and execute malicious actions.
- Exploitation for Client Execution: Exploiting software vulnerabilities that allow the attacker to execute code on the system.
Why It Matters: If the attacker can’t execute their code, they can’t advance their attack. Endpoint detection and response (EDR) solutions, anti-virus, and behavior-based analysis tools can help identify and stop malicious execution.
- Persistence: Attackers want to maintain their access to the target system, even if the system is rebooted or security defenses are applied. Persistence techniques allow the attacker to stay hidden and keep their foothold for as long as possible.
Common Techniques:
- Registry Run Keys/Startup Folders: Adding malicious programs to locations that automatically run at system startup.
- Scheduled Task/Job: Creating tasks that will automatically execute the attacker’s code at specified times.
- Account Manipulation: Creating or modifying user accounts with elevated privileges to maintain access.
Why It Matters: Persistence techniques are used to ensure the attacker can keep coming back. Security teams often use privilege management and regular system audits to spot unusual accounts or scheduled tasks that don’t belong.
- Privilege Escalation: Attackers often seek higher levels of access or control over the system. Privilege escalation allows the attacker to move from a lower-privilege account (like a regular user) to a higher-privilege one (like an administrator) to gain more control over the environment.
Common Techniques:
- Exploitation of Vulnerability: Exploiting software flaws to gain elevated permissions.
- Process Injection: Injecting code into legitimate processes to escalate privileges.
- Bypassing User Account Control (UAC): Using techniques to bypass Windows’ UAC feature and gain admin rights.
Why It Matters: Privilege escalation gives attackers broader access, making it easier for them to move laterally within a network. Implementing strong access controls and regular patching can mitigate this risk.
- Defense Evasion: Attackers don’t want to be caught, so they use various tactics to evade detection by security defenses. This can include disabling security tools, obfuscating code, or deleting logs to cover their tracks.
Common Techniques:
- Obfuscated Files or Information: Hiding the true nature of files or communications to avoid detection.
- Disabling Security Tools: Turning off antivirus, EDR, or firewalls to prevent detection.
- File Deletion: Removing files or logs that could reveal the attacker’s presence.
Why It Matters: Defense evasion helps attackers stay hidden while they continue their attack. Keeping security tools up to date, using tamper-proof logging, and employing multiple layers of defense can reduce the effectiveness of these techniques.
- Credential Access: Attackers often need to steal credentials (usernames and passwords) to move further into a network or access sensitive data. Credential access tactics involve capturing or guessing valid login information for accounts.
Common Techniques:
- Credential Dumping: Extracting credentials stored in memory, files, or the registry.
- Brute Force: Trying multiple combinations of passwords until the correct one is found.
- Keylogging: Recording keystrokes to capture passwords as they are typed by the user.
Why It Matters: Credential access is critical for attackers to gain more control and move laterally within the network. Implementing multi-factor authentication (MFA), enforcing strong password policies, and monitoring for unusual login activities are effective countermeasures.
- Discovery: Once attackers have gained access to a system, they need to learn more about the environment to plan their next move. In this stage, they perform reconnaissance within the compromised network, searching for additional targets, sensitive data, or security weaknesses.
Common Techniques:
- System Network Configuration Discovery: Gathering information about the network structure, connected devices, and configurations.
- File and Directory Discovery: Searching for sensitive files and directories that might hold valuable data.
- Account Discovery: Identifying user accounts and their associated privileges to find high-value targets.
Why It Matters: Discovery is critical for attackers to expand their attack. Using network segmentation, monitoring for unusual user behavior, and employing tools that alert on reconnaissance activities within the network can help identify and stop attackers before they escalate.
- Lateral Movement: In this phase, attackers move from the initially compromised system to other systems within the network. This helps them expand their control, access more resources, or find high-value data. Lateral movement is typically done using stolen credentials, remote services, or exploitation of vulnerabilities.
Common Techniques:
- Remote Desktop Protocol (RDP): Using RDP to access other systems on the network.
- Pass the Hash: Using stolen hashed credentials to authenticate to other systems without needing the plaintext password.
- Windows Admin Shares: Exploiting Windows file shares to move laterally within the network.
Why It Matters: Once attackers start moving laterally, they can potentially access critical systems and sensitive data. Limiting lateral movement through network segmentation, monitoring internal traffic, and using strong identity management controls (such as multi-factor authentication) can help reduce the risk.
- Collection: After moving laterally and discovering valuable data, attackers focus on collecting that data. This includes gathering files, screenshots, keylogging data, and other forms of information that can be useful for their objectives, whether it’s exfiltration, ransom, or further exploitation.
Common Techniques:
- Data from Local System: Copying files or capturing information directly from the compromised system.
- Input Capture: Using keyloggers or input scrapers to collect typed data, including passwords.
- Automated Collection: Setting up scripts or tools that automatically gather files, screenshots, and other data.
Why It Matters: Collection is the step before the data leaves your network. Endpoint protection tools, data loss prevention (DLP) solutions, and monitoring for abnormal file access patterns can help prevent attackers from successfully gathering sensitive information.
- Command and Control (C2): In the C2 phase, attackers establish communication with external servers they control. This connection allows them to remotely command the compromised systems, send additional payloads, or exfiltrate data. These communications can be disguised as legitimate network traffic, making detection challenging.
Common Techniques:
- Commonly Used Port: Using standard ports (like HTTP or HTTPS) to blend in with regular network traffic.
- Domain Fronting: Masking traffic behind legitimate web services to hide the attacker’s true command and control server.
- Encrypted Channel: Encrypting the communication to make it harder for network defenders to analyze the data being transmitted.
Why It Matters: Disrupting the C2 phase can prevent attackers from controlling compromised systems. DNS filtering, anomaly-based network monitoring, and blocking outbound traffic to known malicious domains are effective defenses in this stage.
- Exfiltration: In this phase, attackers take the data they’ve collected and move it outside the target network. The stolen data may include sensitive corporate information, personal data, or intellectual property. Attackers use various methods to exfiltrate data without being detected.
Common Techniques:
- Exfiltration Over Web Service: Uploading data to cloud services, web-based applications, or external websites.
- Data Compressed: Compressing data to reduce its size and make it easier to exfiltrate unnoticed.
- Scheduled Transfer: Automating data transfers at specific intervals to avoid detection.
Why It Matters: Exfiltration is the stage where the attacker gets the payoff from the attack. Preventing this is critical to limiting damage. Security teams can implement data loss prevention (DLP) solutions, monitor for abnormal outbound traffic, and encrypt sensitive data to mitigate exfiltration risks.
- Impact: The final phase of the attack is where the attacker achieves their objective. This could involve destroying data, encrypting systems for ransom (ransomware), disrupting operations, or altering business-critical data. The goal is to maximize the impact on the target organization.
Common Techniques:
- Data Destruction: Deleting or corrupting data to cause irreparable harm to the organization.
- Ransomware: Encrypting data or entire systems and demanding a ransom for decryption.
- Defacement: Altering websites, files, or public-facing systems to spread propaganda or damage the organization’s reputation.
Why It Matters: The impact phase represents the culmination of the attack. Ensuring that systems are regularly backed up, using strong encryption, and having a well-practiced incident response plan can help minimize the effects of this phase.
- Execution (Cross-System Movement): Attackers often need to execute commands across multiple systems after they’ve moved laterally. This allows them to extend their control to additional systems, plant more malicious software, or set up additional persistence mechanisms.
Common Techniques:
- Remote Services Execution: Executing commands on remote systems via SSH, RDP, or other remote services.
- Windows Management Instrumentation (WMI): Using WMI to execute commands across Windows environments.
- Third-Party Software: Leveraging installed third-party software to execute code on other systems.
Why It Matters: Execution across multiple systems allows attackers to broaden the scope of their control. Strong access controls, endpoint monitoring, and behavioral analysis tools can help detect and block these activities.
- Post-Exploitation Activity: After successfully gaining and maintaining access, attackers engage in post-exploitation activities. This might include elevating privileges, spreading laterally, setting up persistence mechanisms, or conducting further reconnaissance.
Common Techniques:
- Persistence Setup: Establishing long-term access to systems through backdoors, scheduled tasks, or compromised accounts.
- Cleanup: Removing evidence of their presence by clearing logs, deleting files, or resetting timestamps.
- Further Data Collection: Identifying new targets within the environment or harvesting more sensitive data.
Why It Matters: Post-exploitation activities enable attackers to deepen their foothold and extend their attack. Security teams need to remain vigilant and monitor for unusual activities even after an initial threat seems to be mitigated.
Case Study: The SolarWinds Supply Chain Attack and the MITRE ATT&CK Framework
The SolarWinds supply chain attack is one of the most significant and far-reaching cyber incidents in recent history. It affected thousands of organizations worldwide, including government agencies and major corporations. By leveraging a sophisticated supply chain compromise, the attackers (believed to be the Russian cyber espionage group APT29) were able to gain access to highly sensitive environments.
Using the MITRE ATT&CK Framework as a reference, we can break down the SolarWinds attack into its various stages and better understand how the attackers progressed through each phase of their operation. This analysis will also demonstrate how the MITRE ATT&CK Framework is applied in real-world scenarios to track, identify, and respond to sophisticated cyberattacks.
- Initial Access
The attackers gained initial access to SolarWinds’ development environment through a supply chain compromise (MITRE ATT&CK ID: T1195). They injected malicious code into the build process of SolarWinds’ Orion software. This tampered code, later distributed as a legitimate software update, created a backdoor (SUNBURST) in the systems of any organization that installed it.
Security Controls:
- Code Review and Integrity Checks: Strong security practices in software development, such as code signing and automated integrity checks, could have detected the malicious changes during the build process.
- Supply Chain Security: Regular audits of third-party suppliers and the use of security controls such as multi-factor authentication (MFA) for access to development environments.
- Execution
Once the compromised Orion software was installed on the victims’ networks, the SUNBURST malware was activated. The attackers used command and scripting interpreters like PowerShell and cmd.exe (MITRE ATT&CK ID: T1059) to execute commands on the victim systems.
Security Controls:
- Endpoint Detection and Response (EDR): EDR solutions can detect abnormal use of scripting interpreters like PowerShell, which often signal malicious activity.
- Application Whitelisting: Restricting the execution of unapproved scripts and binaries can prevent unauthorized code from running.
- Persistence
The attackers established persistence by using techniques such as account manipulation and scheduled tasks (MITRE ATT&CK ID: T1053) to ensure that they would maintain access to the compromised systems, even after system reboots or temporary remediation efforts.
Security Controls:
- Privilege Management: Enforcing least privilege access and regularly auditing user accounts can limit an attacker’s ability to create or manipulate accounts.
- Anomaly Detection: Monitoring for the creation of new scheduled tasks or unauthorized changes to accounts can help identify persistence mechanisms.
- Privilege Escalation
After gaining a foothold, the attackers escalated their privileges to gain administrative control over key systems. They used methods like exploiting public-facing applications and manipulating privileged accounts (MITRE ATT&CK ID: T1068).
Security Controls:
- Patch Management: Regularly applying patches to public-facing systems reduces the risk of exploitation.
- Multi-Factor Authentication (MFA): Requiring MFA for all privileged accounts can thwart efforts to escalate privileges even if credentials are compromised.
- Defense Evasion
The attackers used a variety of defense evasion techniques, such as disabling security tools, timestomping (MITRE ATT&CK ID: T1070), and obfuscating commands to avoid detection by security teams. They manipulated Windows Event Logs and masqueraded their malware as legitimate services to blend into the background noise of the system.
Security Controls:
- Behavioral Analytics: Monitoring for unusual behavior, such as disabled security tools or log tampering, can help identify sophisticated evasion tactics.
- Immutable Logs: Configuring logs to be write-once-read-many (WORM) can prevent attackers from tampering with historical records.
- Credential Access
The attackers used techniques like credential dumping (MITRE ATT&CK ID: T1003) to extract credentials from the memory of compromised systems. This allowed them to gain further access to high-value targets, such as email servers and cloud environments like Microsoft 365.
Security Controls:
- Credential Vaulting: Storing credentials securely in a vault rather than in memory reduces the chance of them being extracted.
- Memory Protection: Advanced endpoint security tools can protect sensitive data stored in memory from unauthorized access.
- Discovery
The attackers performed extensive network discovery (MITRE ATT&CK ID: T1046) to map out the victim’s internal infrastructure and identify valuable targets, such as domain controllers and sensitive data repositories.
Security Controls:
- Network Segmentation: Segmenting networks and restricting communication between sensitive systems limits an attacker’s ability to freely discover and target resources.
- Intrusion Detection Systems (IDS): Monitoring network traffic for signs of reconnaissance and lateral movement can help detect attacks in the discovery phase.
- Lateral Movement
Using the credentials they had stolen, the attackers moved laterally through the network via methods such as Remote Desktop Protocol (RDP) (MITRE ATT&CK ID: T1021) and Windows Admin Shares (MITRE ATT&CK ID: T1077). This allowed them to access more systems and expand their control over the network.
Security Controls:
- Lateral Movement Detection: Tools that detect unusual lateral movement, such as accessing new machines or accounts, can help identify attacks in progress.
- Network Isolation: Limiting remote access tools like RDP to only essential systems and enforcing strict controls can minimize opportunities for lateral movement.
- Collection
Once the attackers had control over key systems, they began collecting valuable data. This included emails, intellectual property, and other sensitive information. They used techniques such as data from local systems (MITRE ATT&CK ID: T1005) and archive via utility (MITRE ATT&CK ID: T1560) to compress and stage the data for exfiltration.
Security Controls:
- Data Loss Prevention (DLP): DLP solutions can monitor and block attempts to collect and move sensitive data.
- User Activity Monitoring: Monitoring for abnormal data access patterns can help detect data collection activities.
- Command and Control (C2)
The attackers communicated with their control servers via web protocols (MITRE ATT&CK ID: T1071) to maintain control over the compromised systems and exfiltrate data. They used domain fronting and other obfuscation techniques to hide their traffic within legitimate web traffic.
Security Controls:
- DNS and Web Filtering: Blocking communication with known malicious domains and analyzing DNS traffic can help detect command and control channels.
- Encrypted Traffic Analysis: Advanced tools that analyze encrypted traffic for anomalies can help identify hidden C2 communications.
- Exfiltration
Finally, the attackers exfiltrated the collected data through web services (MITRE ATT&CK ID: T1567). This was done using encrypted communication channels to blend in with normal web traffic, making detection difficult.
Security Controls:
- Outbound Traffic Monitoring: Monitoring for large or unusual outbound data transfers, especially to unfamiliar web services, can help detect data exfiltration attempts.
- Network Traffic Analysis: Analyzing network traffic for anomalies in data volume, destinations, and types of communication can reveal exfiltration in progress.
The SolarWinds attack is a textbook example of a sophisticated, multi-stage cyber operation that leveraged advanced techniques to compromise thousands of organizations. By using the MITRE ATT&CK Framework, security teams can better understand the tactics, techniques, and procedures (TTPs) used by attackers like APT29 and develop targeted defenses to stop them at various stages of the attack chain. From initial access to exfiltration, each phase of the SolarWinds attack demonstrates the importance of having layered defenses and strong monitoring capabilities to detect and disrupt cyber threats.
Cybersecurity Basics to Minimize Risk from MITRE ATT&CK Tactics
Defending against the various tactics outlined in the MITRE ATT&CK Framework requires a combination of proactive measures, continuous monitoring, and a strong security culture. While sophisticated attacks like the SolarWinds breach can be difficult to completely prevent, there are foundational cybersecurity practices that can significantly reduce your exposure to risk. Here are some key strategies to minimize the impact of common attack tactics:
- Patch Management: Regularly updating software and systems is one of the simplest but most effective ways to reduce vulnerabilities. Cyber attackers often exploit known weaknesses that could have been patched. Make sure you have an automated patch management system in place to address vulnerabilities promptly.
- Multi-Factor Authentication (MFA): Adding an extra layer of security to accounts by requiring multi-factor authentication can prevent attackers from gaining access to systems even if they manage to steal credentials. MFA is particularly effective at mitigating tactics like credential dumping and privilege escalation.
- Network Segmentation: Dividing your network into segments ensures that even if attackers gain access to one part of the network, they have a harder time moving laterally to other areas. Critical systems and sensitive data should be isolated with strict access controls in place, limiting potential damage in the event of a breach.
- Endpoint Detection and Response (EDR): EDR tools provide real-time monitoring and analysis of endpoint activities, helping detect and respond to suspicious behaviors such as unauthorized execution, persistence mechanisms, or lateral movement. This is a key defense against a wide range of MITRE ATT&CK tactics.
- User Awareness and Training: Human error is often the weakest link in cybersecurity. Regular training programs can educate employees about phishing, social engineering, and other tactics that attackers use to gain initial access. Employees should be encouraged to report suspicious activities and regularly tested with phishing simulations.
- Incident Response Planning: Having a well-developed incident response plan ensures that your organization can react quickly and effectively in the event of a breach. This plan should be tested regularly and updated to reflect the latest threats and trends. Knowing who to contact, what steps to take, and how to contain an attack is critical to minimizing its impact.
- Data Encryption: Encrypting sensitive data both at rest and in transit ensures that even if attackers manage to exfiltrate data, it remains unreadable and unusable. Strong encryption protocols, combined with strict key management, can protect your most valuable information from prying eyes.
- Monitoring and Logging: This means actually logging and actually looking at your logs… Comprehensive logging and monitoring across the network and endpoints are essential for detecting abnormal activity. Logs should be analyzed in real time using tools like security information and event management (SIEM) systems, and these logs should be stored in a way that prevents tampering. Anomalous behavior can often be an early indicator of a compromise.
- Least Privilege Principle: Ensure that employees and systems only have access to the resources they absolutely need. The least privilege principle limits the scope of what attackers can do if they gain access to a low-privilege account. Regular reviews of permissions and accounts can help maintain this control.
Wrapping It All Up
The SolarWinds attack highlighted just how advanced and determined cyber adversaries can be, but it also underscored the importance of layered defense strategies. By implementing basic cybersecurity practices, such as timely patching, multi-factor authentication, network segmentation, and user training, organizations can drastically reduce their risk of falling victim to sophisticated attacks. Cybersecurity isn’t just about having the best tools; it’s about fostering a culture of vigilance and preparedness across all levels of an organization. With a solid foundation of best practices and a clear understanding of common adversary tactics, organizations can be better equipped to face emerging threats and protect their most valuable assets.